User-Centric Information-Flow Security
Even as modern computing systems allow the manipulation and
distribution of massive amounts of information, users of these
systems are unable to manage the confidentiality of their data in a
practical fashion. Conventional access control security mechanisms
cannot prevent the illegitimate use of of privileged data once
access is granted. For example, information provided by a user
during an online purchase may be covertly delivered to malicious
third parties by an untrustworthy web browser. Information-flow
security (IFS) mechanisms provide protection against such leaks of
confidential data by tracking the
What is RIFLE? RIFLE is a runtime information-flow security system that is made up of:
Binary Translator - converts conventional binaries into an IFS programIFS Architecture - executes IFS programs and efficiently tracks information flowSecurity Enhanced OS - uses information-flow tracking to enforce user policies
 How is RIFLE different from existing IFS
systems? RIFLE is the first information-flow system designed
from the user's perspective. Existing IFS mechanisms enforce
information-flow policies for programs written in
How is RIFLE different from existing IFS
systems? RIFLE is the first information-flow system designed
from the user's perspective. Existing IFS mechanisms enforce
information-flow policies for programs written in
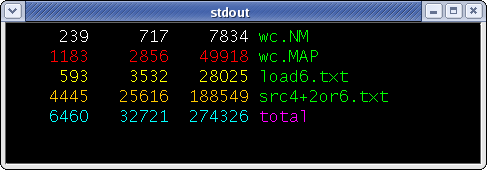
 RIFLE in Action. The figures on
the right show RIFLE in action. The first figure shows simulation
output of the program wc. Each file used had a distinct
owner. The colors in the figure represent the different data owners
on each byte of output. It shows that the data from one file does
not leak into word counts of other files. The total word count is
colored blue, indicating that information from multiple owners was
used in its computation.
RIFLE in Action. The figures on
the right show RIFLE in action. The first figure shows simulation
output of the program wc. Each file used had a distinct
owner. The colors in the figure represent the different data owners
on each byte of output. It shows that the data from one file does
not leak into word counts of other files. The total word count is
colored blue, indicating that information from multiple owners was
used in its computation.
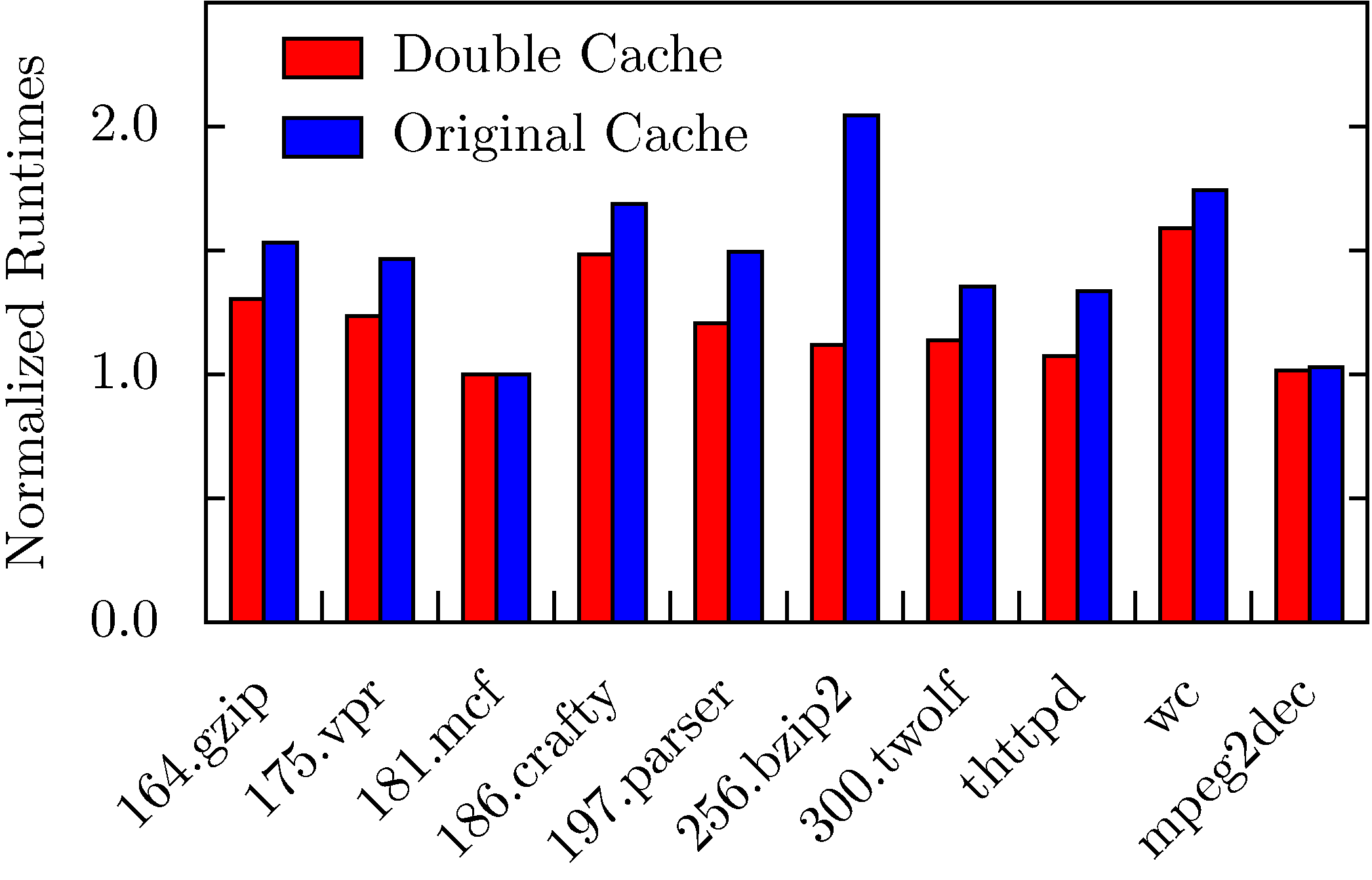
For more information, see our paper in MICRO-37.
